Powershell Determine if Bitlocker Drive is Locked and Continue
In my last post, I outlined how you can enable BitLocker with PowerShell and manage key protectors. Today, I will cover BitLocker management with PowerShell. In particular, I will describe how you can unlock, suspend, resume, and disable BitLocker with PowerShell.
- Author
- Recent Posts
![]()
Manage BitLocker auto unlock with PowerShell ^
When you have multiple data drives attached to your computer that are encrypted using BitLocker, you might want to unlock them automatically once the OS drive is decrypted using TPM, PIN, or a startup key. The auto-unlock feature works only with data drives.
Enable auto unlock
To enable auto-unlock for a particular volume, use the following command:
Enable-BitLockerAutoUnlock -MountPoint "D:"

Enable auto unlock for a BitLocker encrypted data volume using PowerShell
To enable auto-unlock for all data drives at once, use the following command:
Get-BitLockerVolume | ? {$_.VolumeType -eq 'Data'} | Enable-BitLockerAutoUnlock 
Enable auto unlock for all BitLocker encrypted data volumes using PowerShell
This command gets all the data volumes on the computer and passes them to the Enable-BitLockerAutoUnlock cmdlet to enable auto-unlock. Remember, auto-unlock does not work with operating system volumes.
Disable auto-unlock
To disable auto-unlock for a specific volume, use the Disable-BitLockerAutoUnlock cmdlet, as shown below:
Disable-BitLockerAutoUnlock -MountPoint "F:"

Disable BitLocker auto unlock for a particular volume using PowerShell
To disable auto-unlock on all data drives at once, use the Clear-BitLockerAutoUnlock cmdlet, which doesn't require any additional parameters.

Disable BitLocker auto unlock for all data volumes at once using PowerShell
Backup key protectors ^
If your computer belongs to an Active Directory domain, you could use the Backup-BitLockerKeyProtector cmdlet to save the recovery password key protector to Active Directory. Once again, you need to specify the key protector using its ID.
$BVol = Get-BitLockerVolume -MountPoint "C" Backup-BitLockerKeyProtector -MountPoint "C" -KeyProtectorId $BVol.KeyProtector[2].KeyProtectorId
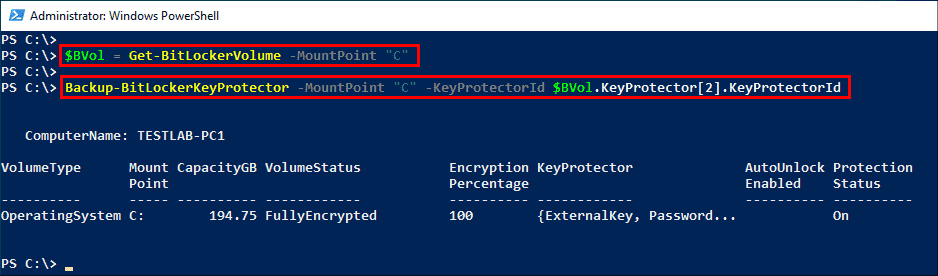
Save the recovery password key protector to Active Directory using PowerShell
Make sure you supply the right array index for the recovery password key protector; otherwise, you will get an error. To learn how to use BitLocker in the Active Directory domain environment in detail, read the series of posts written by Kyle Beckman.
Manually lock and unlock encrypted drives ^
If you do not want to enable auto-unlock for data drives, the BitLocker PS module offers the Lock-BitLocker and Unlock-BitLocker cmdlets. These cmdlets let you control access to encrypted volumes manually on demand.
To manually lock a data volume, use the following command:
Lock-BitLocker -MountPoint "D:"
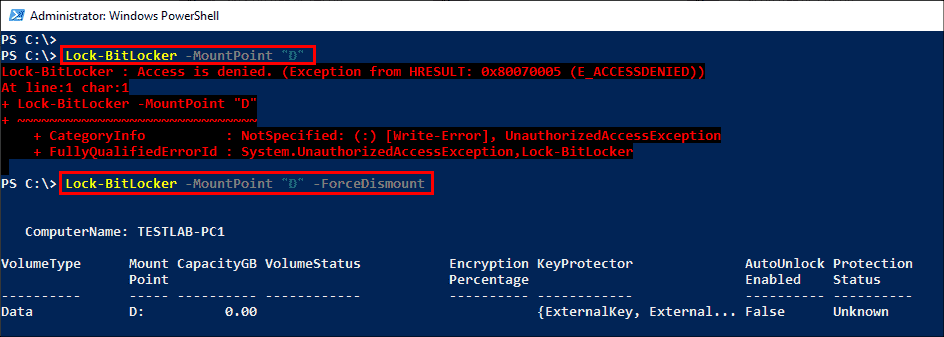
Manually lock a BitLocker volume using PowerShell
You will receive an error if the drive is currently in use. In this case, you could use the -ForceDismount parameter to override. Use this option only when necessary, as it could result in data loss. It is a good idea to gracefully close all apps and files before using the Lock-BitLocker command.
To unlock the encrypted data volume, use the following command:
Unlock-BitLocker -MountPoint "D:" -RecoveryKeyPath "E:\2D64E750-ED79-425A-A084-2CCE6B2F8CC6.BEK"
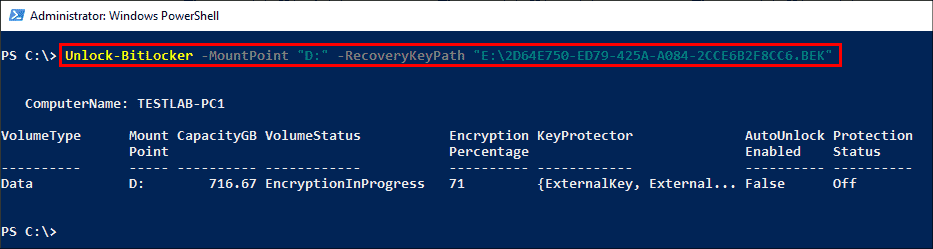
Manually unlock a BitLocker volume using PowerShell
You need to specify the right key protector using a switch parameter to unlock the drive. To unlock the drive using a password, make sure you generate a secure string with the help of the ConvertTo-SecureString cmdlet.
Suspend/Resume BitLocker protection ^
During a system or firmware upgrade, you might want to temporarily suspend BitLocker protection. Note that suspending BitLocker doesn't mean the data is no longer encrypted. Data is still encrypted, but BitLocker will make the decryption key available to everyone. The Suspend-BitLocker cmdlet is used to suspend BitLocker protection on a specific drive.
By default, BitLocker suspension resumes automatically when the computer is restarted, but you could use the -RebootCount parameter to specify the number of reboots when BitLocker protection resumes.
Suspend-BitLocker -MountPoint "C" -RebootCount 2

Suspend BitLocker protection on a volume using PowerShell
To make the BitLocker suspension indefinite until you manually resume it, set the value of the -RebootCount parameter to 0. File Explorer displays a warning on a volume with suspended BitLocker protection.

File Explorer showing a suspended BitLocker volume
To resume the protection manually, use the following command:
Resume-BitLocker -MountPoint "C"

Resume BitLocker protection on a volume using PowerShell
To resume protection on all drives, use the Get-BitLockerVolume | Resume-BitLocker command.
Disable BitLocker ^
To permanently decrypt a volume and disable BitLocker protection on it, use the Disable-BitLocker cmdlet as shown below:
Disable-BitLocker -MountPoint "D:"

Disable BitLocker protection and decrypt a volume using PowerShell
Note that if you're decrypting an operating system drive containing auto-unlocking keys, you need to use Clear-BitLockerAutoUnlock first. To disable BitLocker and decrypt all the volumes on a computer, use the following commands:
Subscribe to 4sysops newsletter!
Clear-BitLockerAutoUnlock Get-BitLockerVolume | Disable-BitLocker

Disable BitLocker and decrypt all volumes using PowerShell
This post was all about the BitLocker PowerShell module. In the next post, I will cover how to fix various errors that you might encounter while working with the BitLocker module.
![]()
hendricksshavessined.blogspot.com
Source: https://4sysops.com/archives/unlock-suspend-resume-and-disable-bitlocker-with-powershell/
0 Response to "Powershell Determine if Bitlocker Drive is Locked and Continue"
Post a Comment